[Update #2] Mission Cyber Sentinel

In this article, I would like to share an update regarding "Mission Cyber Sentinel", a mission that was started with the goal of securing 250,000+ websites by identifying vulnerability in widely used web application software(s).
Introduction
Mission Cyber Sentinel is a Canadian cybersecurity initiative dedicated to protecting over 250,000 websites and safeguarding more than 25 million users worldwide.
When I first began “Mission Cyber Sentinel” on January 11th 2025, I was doing it alone until I met Luke Smith & Alasdair Gorniak, great hackers from the UK. With their collaboration my goal of securing up to 250,000 online assets became much easier because their contributions have directly impacted this project.
What are online assets?
An online asset refers to a website, web application, server, or other internet-connected system running specific software. For example, when we say that Microweber is used by over 995 assets, it means the software is installed or actively in use on more than 995 websites, servers, mobile applications, or networks.
Our goal
In this article, we would like to share unofficial statistics that show the impact of our work. Unofficial means that we won’t be able to disclose details about our findings yet.
Mission Cyber Sentinel’s goal was to find vulnerabilities in widely used open-source software (mostly web apps) and report them to their vendors and MITRE for CVE assignment. For example, finding a Server-side request forgery vulnerability in a CMS used by 1,541 sites would count towards the goal of securing 250,000 online assets.
As a result of reporting findings, I have been awarded with 6 CVEs in less than 2 months with more on the way. You can find out about 5 of them here:
- https://hkohi.ca/vulnerability/13
- https://hkohi.ca/vulnerability/12
- https://hkohi.ca/vulnerability/2
- https://hkohi.ca/vulnerability/1
- https://hkohi.ca/vulnerability/3
Vulnerability submission wait period
We understand that sometimes a vendor might dispute a report or claim that the vulnerability was not found on their software(s) and it happens very often, either because it was a duplicate or because the developers don’t think it’s a major issue.
I can recall that when I had first reported two vulnerabilities to ezBookkeeping, they argued that it’s not an issue but after I was assigned CVE(s), they eventually fixed their issues. You can see a very transparent discussion about it here:
https://github.com/mayswind/ezbookkeeping/issues/33#issuecomment-2708924026
For this reason we are not going to mention which vulnerabilities were found in every software but instead we are just going to list the targets and their usage stats.
Official results will be available within the next 90 days or more.
The reason that we go over usage is because we want to demonstrate that the vulnerabilities we find are not useless, they impact real active systems and users.
Current status of our mission
As of today, March 10th 2025, we have identified enough vulnerabilities to impact a combination of up to 376,092+ websites globally. Assuming that each site has at least 100 visitors, we have safeguarded information of 37,609,200+ users from cyber-attacks.
Alasdair Gorniak’s contribution to Mission Cyber Sentinel
Alasdair Gorniak has identified vulnerabilities in UltraMobile - according to their Wikipedia page, By 2016, Ultra Mobile products were available in over 25,000 retail stores in the US, including Target and 7-Eleven.
Additionally, Alasdair has identified a vulnerability in NetSweeper Firewall (CVE-2025-25497), a company that has protected over 1.2 billion users globally from all types of threats such as malware, viruses and proxies.
Luke Smith’s contribution to Mission Cyber Sentinel
Luke has contributed to identifying a vulnerability in OnlyOffice, a platform used by over 9,933+ websites and potentially many more are using it internally.
According to Wikipedia, OnlyOffice is delivered either as SaaS or as an installation for deployment on a private network. Its cloud solutions cater to businesses, educational institutions, and government agencies, offering advanced collaboration features. Created for online document collaboration, OnlyOffice also offers desktop editors for offline work.
Status report
The following is the list of findings by each contributor to Mission Cyber Sentinel:
# | Name | Affected assets | Reporter |
|---|---|---|---|
1 | Open Journal System | 52,320+ | Hamed Kohi |
2 | OnlyOffice | 9,933+ | Hamed Kohi & Luke Smith |
3 | Typo3 CMS | 182,087+ | Hamed Kohi |
4 | Vvveb | 163+ | Hamed Kohi |
5 | Fuel CMS | 100+ | Hamed Kohi |
6 | Anqi CMS | 100+ | Hamed Kohi |
7 | ezBookkeeping | 100+ | Hamed Kohi |
8 | Easy Appointments | 1,269+ | Hamed Kohi |
9 | NukeViet | 3,174+ | Hamed Kohi |
10 | Apache JSP Wiki | 26+ | Hamed Kohi |
11 | Microweber | 995+ | Hamed Kohi & Luke Smith |
12 | Contao CMS | 76,332+ | Hamed Kohi |
13 | NetSweeper Firewall | 27,200 - 31,840 | Alasdair Gorniak |
14 | Close CRM | 500+ | Alasdair Gorniak |
15 | Zen Cart | 22,193+ | Hamed Kohi |
For the most part we used BuiltWith.com to get these usage stats but for some other products like OJS, we use their own website:
https://rpubs.com/saurabh90/ojs-stats-2023
The following map shows top 10 countries affected by the vulnerabilities we have identified:
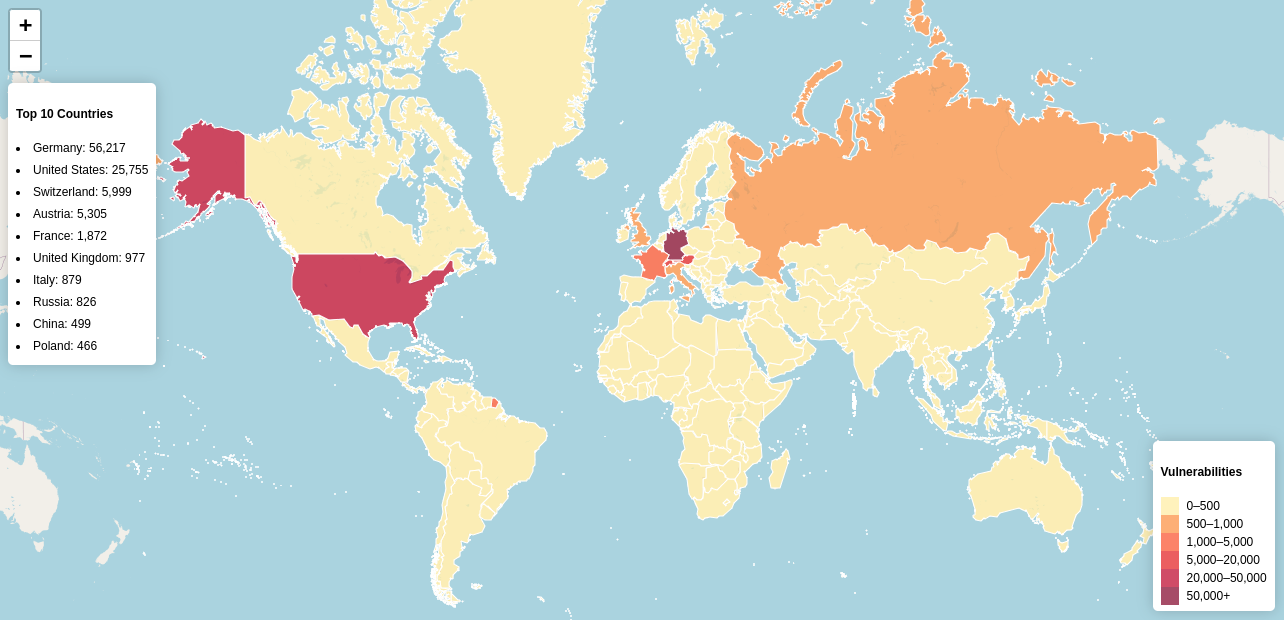
Acknowledgment
Cybersecurity is a collaborative effort, we would like to thank MITRE for their assistance in analyzing vulnerabilities and assigning CVEs. You are doing a great job, thank you.
Additionally, I would like to thank Luke Smith and Alasdair Gorniak for becoming a part of Mission Cyber Sentinel.
Collaboration opportunities
If you are interested in becoming part of our missions, you can get in touch with me. We have two requirements for anyone trying to join us:
- You should have completed course work for CPTS OR CBBH OR you have found valid vulnerabilities in bug bounty programs OR you have at least one CVE assigned to your name (any of these)
- You have a LinkedIn profile that we can see and verify that you are a real person; we prefer to work with people who aren’t anonymous; exceptions apply when you have been awarded with CVE(s)
It’s true that web apps are widely used but so are servers, AI/ML technologies, firewalls, industrial plant monitoring systems, physical access control systems, cameras, routers, operating systems, Desktop apps, mobile apps, kiosk systems in airports, smart home systems, clinical/medical software, and tons of other systems used in, factories, emergency services, governments, power plants, hospitals and the military.
We are moving towards identifying vulnerabilities in some of the most critical systems in existence.
Posted on: March 10, 2025 03:44 PM