Contao’s Laughable “Bug Bounty” Program and Self-Assigned CVEs
The following document describes Contao's CVE fraud in great detail:
https://hkohi.ca/uploads/contao_cve_fraud.pdf
The article that you are about to read has some of my personal views which may distract the reader from the most important issue at hand: CVE Fraud. You can still read the article for the laughs though.
Intro
Let’s talk about Contao’s so-called bug bounty program and their utterly farcical CVE assignment practices on GitHub. Spoiler alert: it’s a self-congratulatory echo chamber masquerading as a security initiative.
On March 10th, 2025, I responsibly reported three vulnerabilities to the Contao team. Here’s the proof:
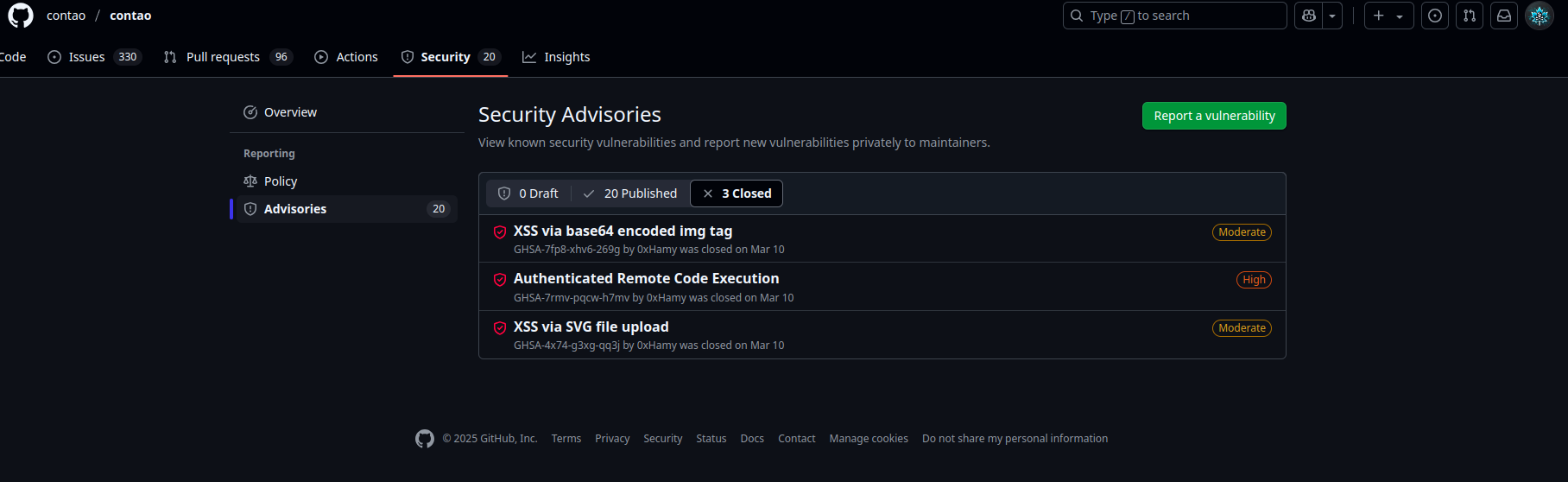
Soon after submitting my report, I discovered that Contao not only claims to run a bug bounty program, but also assigns their own CVEs. Sounds convenient, doesn’t it?
Upon digging through their security advisories, I noticed something hilariously suspicious: all the CVEs are attributed to the same person: @leofeyer. You read that right. Every. Single. One.
Connecting the dots
Now, let’s connect some very obvious dots: Leo Feyer is not just a "researcher", he’s a Contao maintainer. Apparently, he plays all the roles in this tragicomedy, he introduces the bugs (presumably by accident, or perhaps for sport), later "discovers" them, then triumphantly shouts "Aha! I found it!" to himself and slaps a shiny new CVE on it. It’s security theater at its most embarrassing.
Compare that to my own track record: my CVEs are vetted and assigned through MITRE or Apache, with multiple respected professionals who can independently vouch for my findings. My discoveries span numerous independent projects, including entire operating systems. Faking those wouldn’t just be difficult, it would be impossible.
But here’s the problem: the CVE system on GitHub is now being abused by amateurs with GitHub access and overblown egos. Enter Leo Feyer and @ausi, the poster children for how not to be a security researcher. Their strategy? Game the system, self-assign CVEs, and collect fake clout from a broken process they themselves are exploiting.
Let’s get specific. One of the vulnerabilities I reported to Contao was an XSS via SVG. It was tracked as GHSA-4x74-g3xg-qq3j and surprise, surprise, it was rejected. Here’s how that discussion went down:
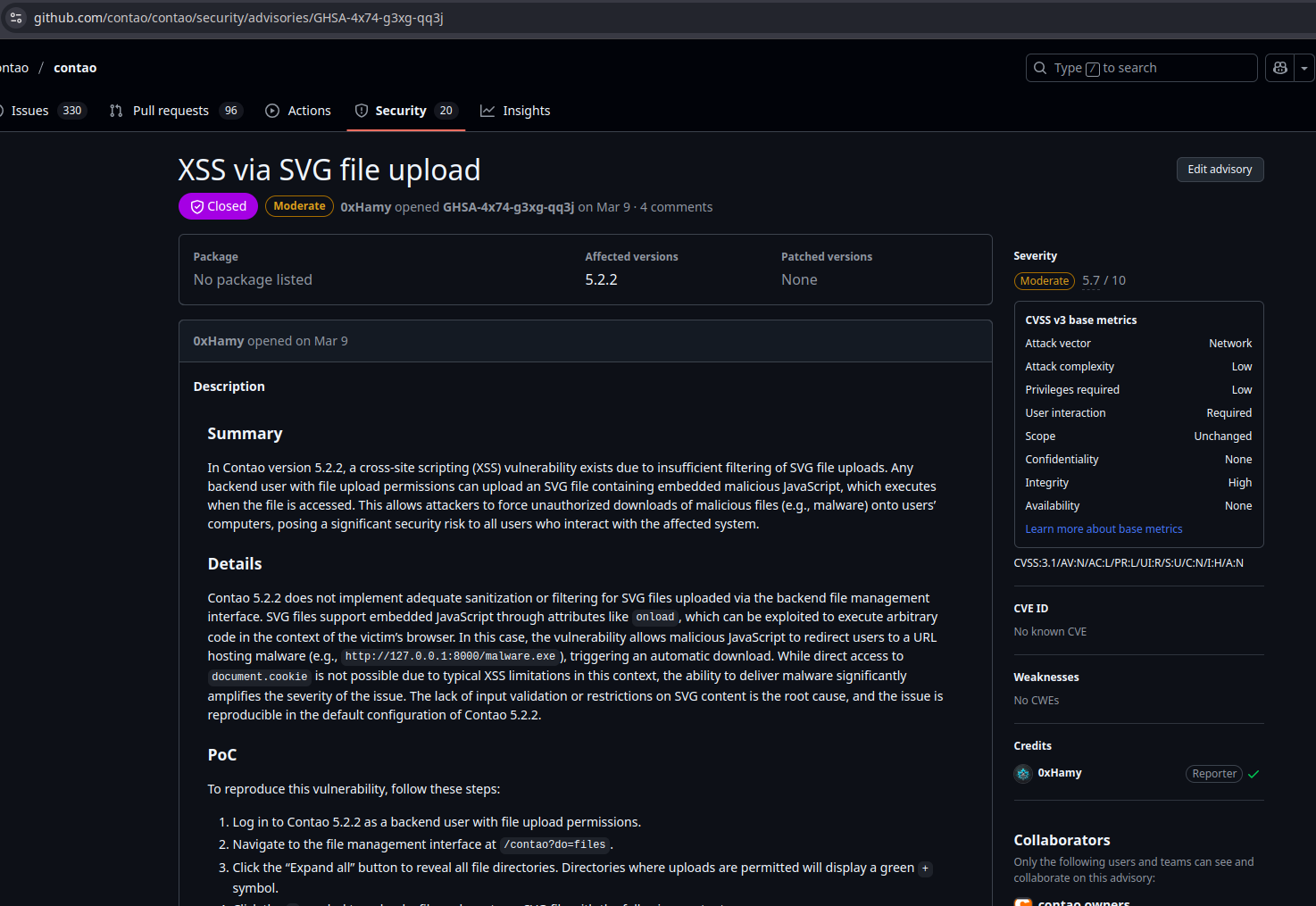
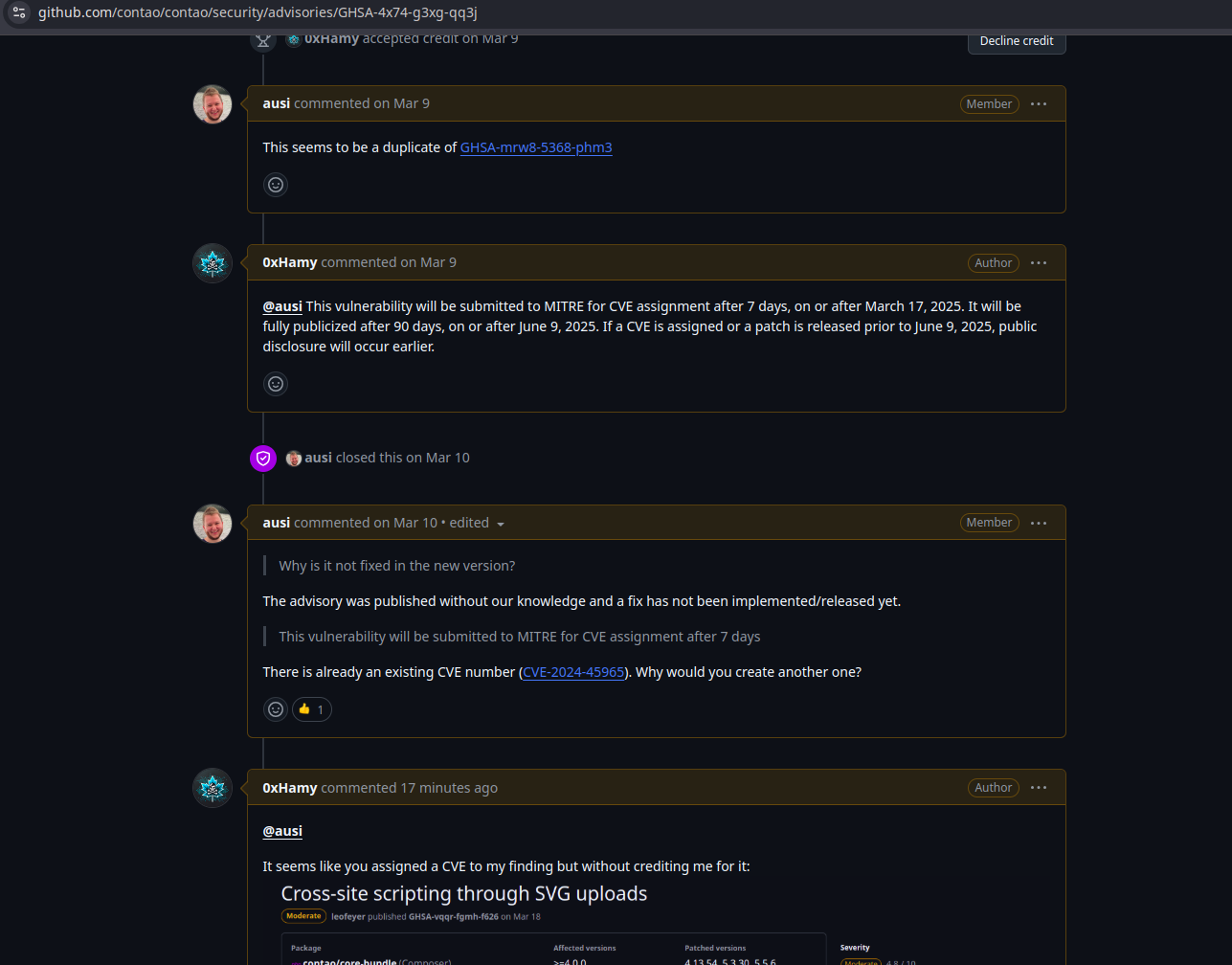
And now for the punchline: Leo Feyer later reported the same XSS via SVG issue and got a CVE for it.
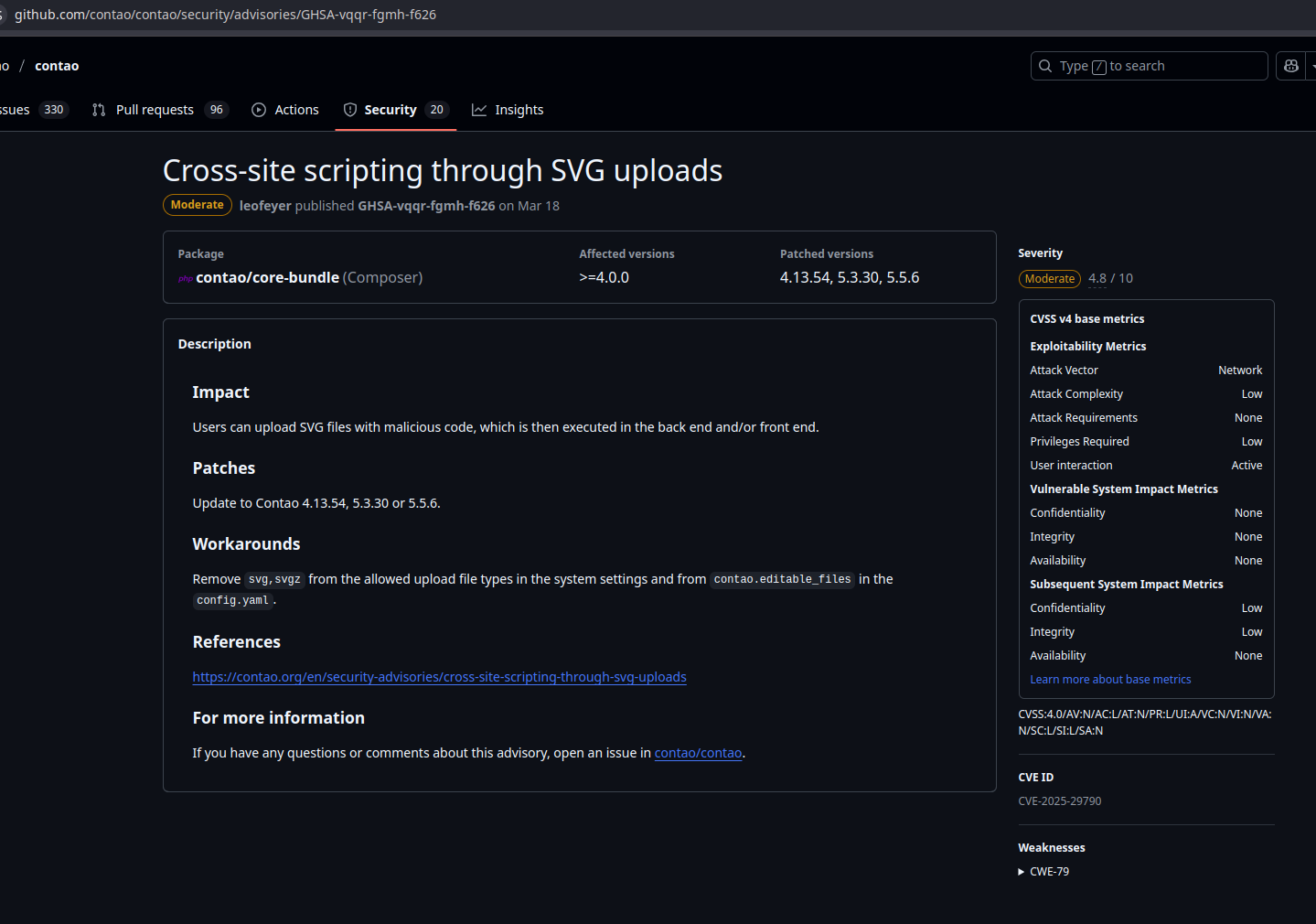
https://github.com/contao/contao/security/advisories/GHSA-vqqr-fgmh-f626
Yes, you read that correctly. The same bug. Different name. Different person. This time with a CVE badge of honor, because when you’re both the gatekeeper and the guest of honor, rules are more like suggestions.
And just to add insult to injury, Contao boasts a “bug bounty program”:
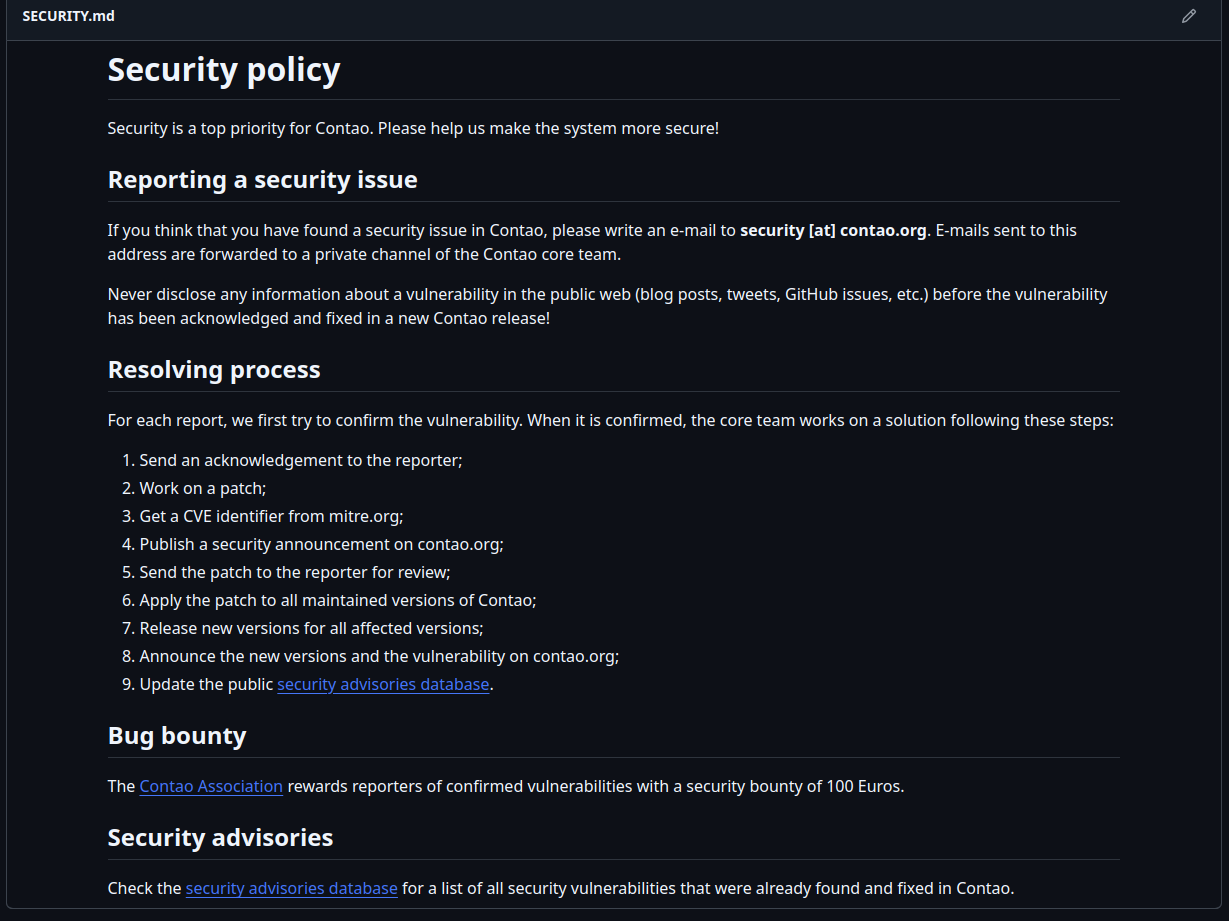
“The Contao Association rewards reporters of confirmed vulnerabilities with a security bounty of 100 Euros.”
Fantastic. Except it’s a complete fabrication. There is no functioning bounty program. No payouts. No public recognition. Just a scammy setup designed to humiliate real security researchers while stealing their work, denying their credit, and padding internal CVE stats for what I can only assume is a sad resume boost.
This isn’t just unethical, it’s embarrassing. Contao’s security process is a parody of itself, built on self-serving antics and a desperate hunger for recognition.
If this is the new standard for vulnerability disclosure, then the industry is in real trouble.
Posted on: May 04, 2025 10:28 PM