We Made a Cyber Army. Kinda.

Hello everyone,
For the past few months, my team and I have been quietly plotting something ambitious, making cybersecurity actually accessible, practical, and just a bit less soul-crushing to get into.
One of the things I’ve been obsessing over (and occasionally losing sleep about) is building a no-fluff, no-theory-dump cybersecurity training platform built specifically for training Canadian cyber operators… and anyone else who’s tired of boring PDFs pretending to be education.
The official launch window for Cyber Mounties was supposed to be between June 21st and June 29th. But in a shocking twist that will surprise absolutely no one who knows me, I launched the website early. As in right now:
Now, don’t panic, we’re still saving the rest of the fun for the original window. Between June 25th and June 29th, I’ll be launching Delta Obscura’s website, this one’s for our team, our research, and the slightly more shadowy side of our work:
To mark this momentous (and completely self-imposed) milestone, I’ve picked a soundtrack:
🎵 https://www.youtube.com/watch?v=-S6FzomfFzQ
Please loop this dramatically before reading further. It sets the tone.
Here’s what we’ve built from scratch, without institutional handouts:
- Cyber Mounties Academy - launched
- Delta Obscura - research division (launching soon)
- Sentinel Vulnerability Database (SVD) - next-gen disclosure system (in progress)
- Obscurank - gamified cyber-RPG for youth training (in bleurprinting phase)
- Global Cybersecurity Missions - real-world vulnerability ops (ongoing)
What started as a solo mission has now evolved into a globally diverse team:
Hamed Kohi (Canada), Luke Smith (UK), Alexandru-Ionuț Răducu (Romania), Alasdair Gorniak (UK), and Daniel Johnson (Nigeria); five cybersecurity minds working voluntarily for a cause bigger than borders.
Unlike most cyber teams, our members aren't anonymous or hiding behind Tor, almost all of our members are full-time working professionals with LinkedIn & public good work.
Progress So Far
Let me introduce you to the men behind the mystery.
1. Cyber Mounties Academy
Launched June 15th, 2025. Our first demo course is live in 5 languages, including English, French, Spanish, German and Portuguese.
Link: https://academy.cyberm.ca https://cyberm.ca
2. Delta Obscura
Led by Luke Smith, this is our global research arm. It exists to as a place where we can collaborate and work with security researchers from any country as long as they remain ethical.
Link: https://delta.cyberm.ca
Estimated launch date: June 25th - June 29th 2025
3. Sentinel Vulnerability Database (SVD)
Led by Daniel Johnson, the Sentinel Vulnerability Database (SVD) is our not-so-humble attempt to fix what’s broken with traditional vulnerability disclosure platforms like GitHub advisories (GHSA) and MITRE’s aging CVE system.
Unlike the usual suspects, SVD is built to be resistant to manipulation, ego-driven patch submissions, and the kind of disclosure theater that gives out CVEs for hardcoded default passwords like it’s Halloween candy. We take things a bit more seriously. So seriously, in fact, that we’re offering $50 CAD to anyone who can find a legitimate flaw in our process, because if you're going to call us out, at least let us buy you lunch.
For some context (and light reading), check out our Contao CVD Fraud write-up, a charming tale of how disclosure systems can be gamed, misused, or just plain ignored.
As our team dives into critical zero-day vulnerabilities in sectors like healthcare, energy, and open-source infrastructure, we need a disclosure platform that doesn’t move at the speed of government paperwork. SVD is built to be faster than MITRE, more transparent than GitHub, and refreshingly free of bureaucratic speed bumps.
And because we like solutions more than drama, SVD requires that anyone reporting a vulnerability also provide a fix. Yes, really. If vendors decide to ghost us or shrug off critical issues, we simply upload a patched version of their software ourselves. We then alert affected users/businesses, because security shouldn’t wait for boardroom approvals or legal teams to "circle back."
It’s not just another disclosure platform, it’s a system designed to actually protect people's data from irresponsible vendors/maintainers and threat actors.
4. Obscurank
A cybersecurity role-playing game designed for youth 13 to 19 year olds, built to gamify learning and recruit top talent. Imagine offensive cyber ops in a simulated, controlled, and safe environment. That’s Obscurank.
It's going to be a little like call of duty, minus the shooting.
5. Global Cybersecurity Missions
Our first mission, Mission Cyber Sentinel is 92% complete as of May 20th, 2025. We’ve identified 30+ zero-days across critical open-source projects, protecting over 230,000 real-world assets.
That’s 23 million+ users indirectly secured, assuming just 100 visitors per asset.
Here is the list of CVEs credit to our team members:
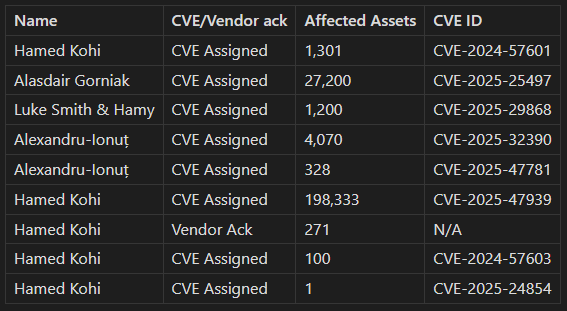
P.S. “Vendor ack” refers to vendor acknowledgement, meaning some of these vulnerabilities were acknowledged and patched by the vendors, but no CVE was assigned.
To be honest, we technically completed the mission within the first three months. We found enough vulnerabilities with a blast radius of over 500,000 websites. But let’s be real, you wouldn’t believe any of it without shiny CVE numbers attached. So we waited.
It’s not that we didn’t do the work. We did. Repeatedly. But without CVEs or vendor acknowledgement, there's no “official” way to prove anything. And now that MITRE has collapsed into a bureaucratic black hole, good luck assigning new CVEs.
That’s exactly why we created SVD, our own disclosure system built to bypass that bottleneck entirely.
6. Cyber Threat Intelligence course
On April 25th 2025, I posted an article about my upcoming CTI course with a demo, the demo was about demonstrating how AI & careful prompt engineering can be used to categorize posts on a fictional Tor marketplace discussing IABs or initial access sales of Canadian businesses.
See demo.
The main course will be launched on Cyber Mounties Academy in July this year.
This course is designed to teach you how to gather actionable cyber threat intelligence from underground hacking forums, specifically, posts that offer initial access to Canadian businesses. Whether you're a curious learner, a threat analyst, or someone trying to make sense of how cybercrime operates in the shadows, this course will give you a practical lens into the world of Initial Access Brokers (IABs) and real-world threat detection.
How It All Fits Together
- Cyber Mounties Academy: Training ground
- Delta Obscura: Research engine & team building
- Sentinel Vulnerability Database: Disclosure backbone
- Obscurank: Talent funnel
- Global Cybersecurity Missions: Impact mechanism
We are essentially building our own private talent pipelines that serves our own interests, and so far our interests have been expressed through missions like cyber sentinel.
We are not affiliated with the RCMP. Yet.
Yes, we know, the name Cyber Mounties Canada might raise a few eyebrows. “Mounties” does have that unmistakable RCMP flavor. But before registering the name in Ontario, we made sure it wouldn’t get us into trouble with The Trademark Act:
(o) the name “Royal Canadian Mounted Police” or “R.C.M.P.” or any other combination of letters relating to the Royal Canadian Mounted Police, or any pictorial representation of a uniformed member thereof.
So, no, we’re not the RCMP. We’re not trying to be the RCMP. We’re not even aiming for a low-budget Netflix adaptation of the RCMP. It’s just a name. That said, we take branding and boundaries seriously, and if anyone at the RCMP has questions, we’re easy to reach at [email protected].
Now, yes, the whole look and feel of Cyber Mounties might come off a bit… tactical. That’s intentional. We’re leaning into the “Cyber Operator” aesthetic, not the usual corporate infosec vibe. And for the record: no, I don’t work for the government. I’m not on contract, not in the reserves, not even lurking in a back office. Everyone assumes I must be, which would honestly be flattering if it came with a pension.
Global expansion plans
In July 2025, we plan to release our Cyber Threat Intelligence course in five languages:
- English
- French
- Spanish
- German
- Portuguese
This multilingual approach allows us to make Cyber Mounties accessible across the Americas and parts of Europe. High-quality, practical cybersecurity education especially offered freely is still rare in many of these regions. Our goal is to make this kind of training widely available, with Canada positioned at the center of that effort.
Looking ahead to 2026, we plan to add five more languages:
- Hebrew
- Arabic
- Chinese
- Korean
- Japanese
Hebrew makes the list for a reason: we’ve taken more than a little inspiration from Unit 8200, Israel’s legendary cyber-intel unit. You know, the one that somehow turns teenagers into nation-state-level hackers before they’re old enough to legally rent a car. Their ability to spot raw talent and weaponize it for national defense is... mildly terrifying and deeply impressive.
We're borrowing the concept minus the uniforms, classified briefings, and, well, actual government authority, and applying it to the civilian world. Think of it as Unit 8200 Lite: same energy, fewer geopolitical consequences.
No, we’re not a military outfit. We don’t have encrypted bunkers, taxpayer funding, or cool call signs. We don’t even have an office espresso machine. But we do believe in a core principle that matters: find sharp minds, train them up, and equip them to do real damage, the good kind in global cybersecurity. Ideally before they go full blackhat out of boredom or spite.
We give them the good stuff: elite training through our academy, research clout via Delta Obscura, and skills assessment through our extremely serious cyber-ops RPG, Obscurank. We also give them clout and recognition, if you want to know what I mean, look up my name (Hamed Kohi) on Google, ChatGPT, Claude or Grok. That's what we give to every member of our team.
What we don’t give them (yet): jobs, pensions, or dental. But hey, dreams have to start somewhere.
Conclusion
I began developing this initiative on January 1st, 2025, and by June 15th, we've established the core structure of the Cyber Mounties pipeline. While the team at Delta Obscura contributed significantly to Mission Cyber Sentinel and the CVE work, I’ve personally led much of the development side.
By the end of 2025, we plan to launch the SVD platform, the Cyber Threat Intelligence course, and Obscurank. In under a year, we’ve created a public, full-stack cybersecurity talent pipeline and contributed over a dozen CVEs, and we’re just getting started.
What we’ve accomplished in scope and speed is rare across startups, nonprofits, and academic programs alike. The mission combines technical skills with long-term vision, disciplined execution, and deep personal commitment.
For me, this work goes beyond a project, it’s a cause I’m fully invested.
Posted on: June 17, 2025 05:13 PM